I recently encountered an issue where a server wouldn’t install any Windows Updates, whether directly from Microsoft, or if downloaded from the Windows Update Catalog. The error message received was “Windows cannot install required files error 0x80070570” and this is how I resolved the error.
From an administrative command prompt I ran the System File Checker using sfc /scannow. This stopped with an error at 36%. The log for sfc is in the %windir%\Logs\CBS folder.
Next, I used the Deployment Image Servicing and Management (DISM) tool to perform a health scan of the Windows system files. Again, I ran this from an administrative command prompt, Dism /Online /Cleanup-Image /ScanHealth, but it showed no errors.

Despite the fact no corruption was detected, I ran the following command to fix corruption, Dism /Online /Cleanup-Image /RestoreHealth. In my case, rather than using Windows Update to retrieve fresh files, I used the /Source switch to point to a copy of the SXS folder from a Windows installation ISO.
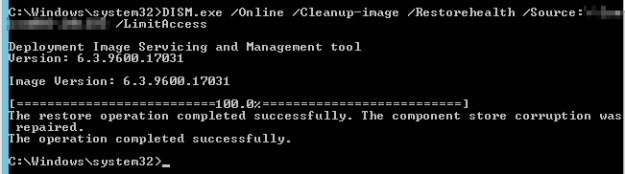
Having fixed the corruption Windows Updates now installed.